Silentless-X Devs Riddle
How to decrypt GPG messages without password and get rewarded
For a context, I do have and education in cybersecurity, so I had some expertise beforehand 🙃
It's all started as with given Discord message my Hertz: 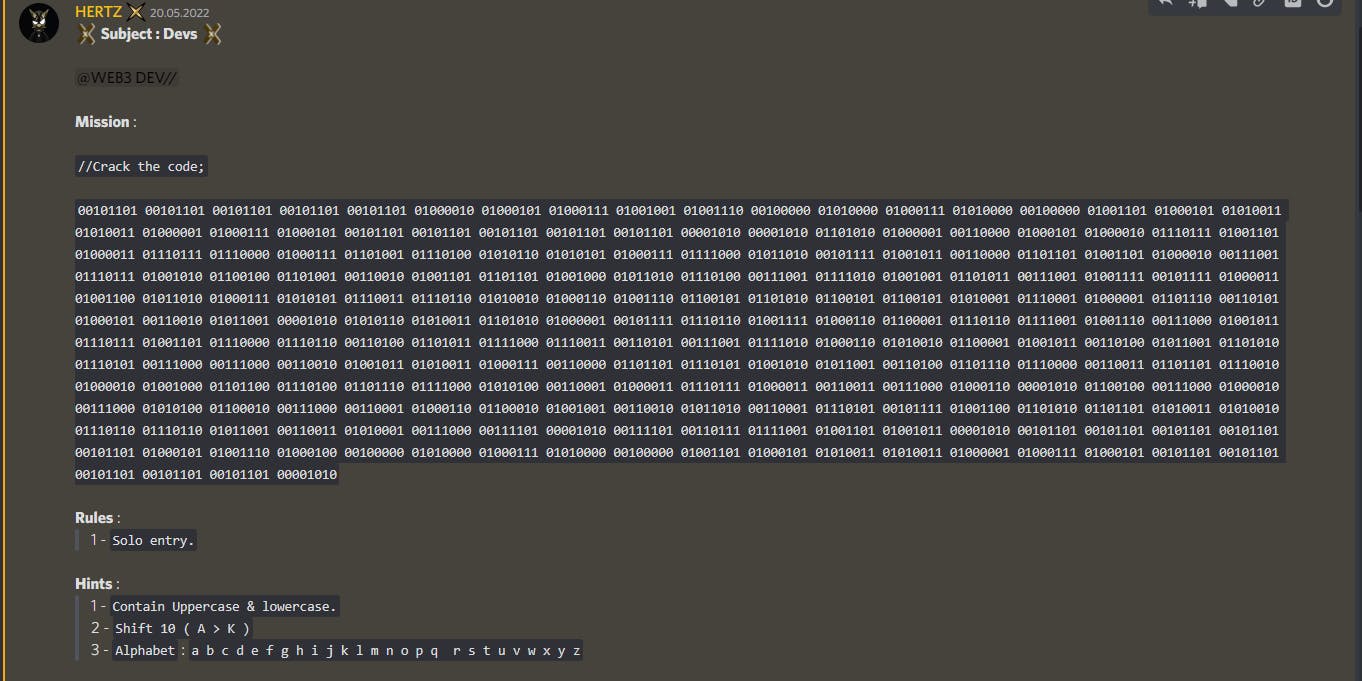
1. Binary message
Clearly this message is a some binary sequence. No fancy tools required, I used first tool, that showed up for "binary to text" - rapidtables.com/convert/number/binary-to-as..
Decoding given message returned into following:
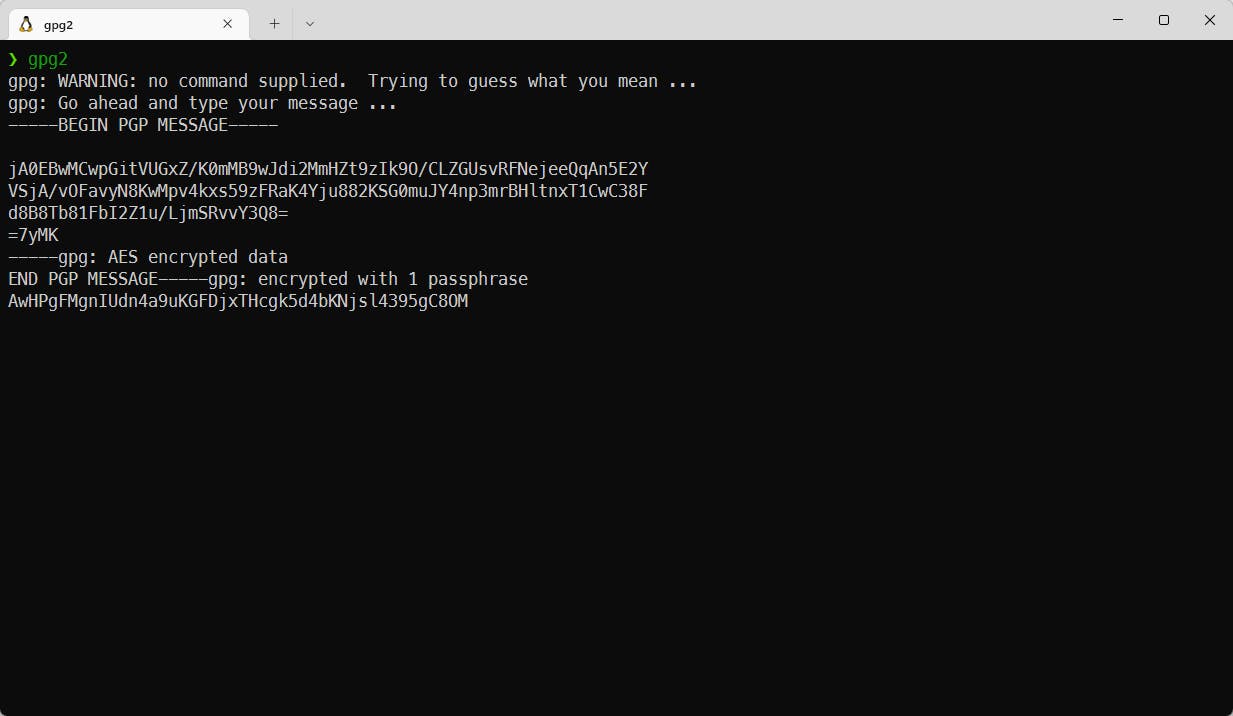
-----BEGIN PGP MESSAGE-----
jA0EBwMCwpGitVUGxZ/K0mMB9wJdi2MmHZt9zIk9O/CLZGUsvRFNejeeQqAn5E2Y
VSjA/vOFavyN8KwMpv4kxs59zFRaK4Yju882KSG0muJY4np3mrBHltnxT1CwC38F
d8B8Tb81FbI2Z1u/LjmSRvvY3Q8=
=7yMK
-----END PGP MESSAGE-----
2. PGP message decoding
Some theory
Decoding PGP message may be confusing, because quick googling for "decrypt pgp message" results into fact, that you need some kind of private key and passphrase. That is not completely true, because PGP is just a software, that used to create such message
PGP (Pretty Good Privacy) is an encryption program that provides cryptographic privacy and authentication for data communication. PGP is used for signing, encrypting, and decrypting texts, e-mails, files, directories, and whole disk partitions and to increase the security of e-mail communications. And being a capable program, it allows to use multiple ciphers.
There are to main "categories" of ciphers: Symmetric and asymmetric.
Symmetric cipher uses same password for encrypting and decrypting message. Think of it as standard Web2 password combination, anyone who got it has access to your account Asymmetric ciphers on the other hand uses so-called public and private keypair together with passphrase. These pairs mathematically paired with each other, so only one public key is paired and represents exact single private key. You can share your public key without worries to other people, so they cat know, that it was you, who encrypted some message. In fact, this is what used it blockchain, your address - is your public key, and your private key is, huh, your private key.
Tackling message decryption
To decrypt this message, I used software, called gpg2. It is a free and open-sourced version of PGP software, mentioned above, commonly used in Linux and Ubuntu distributions
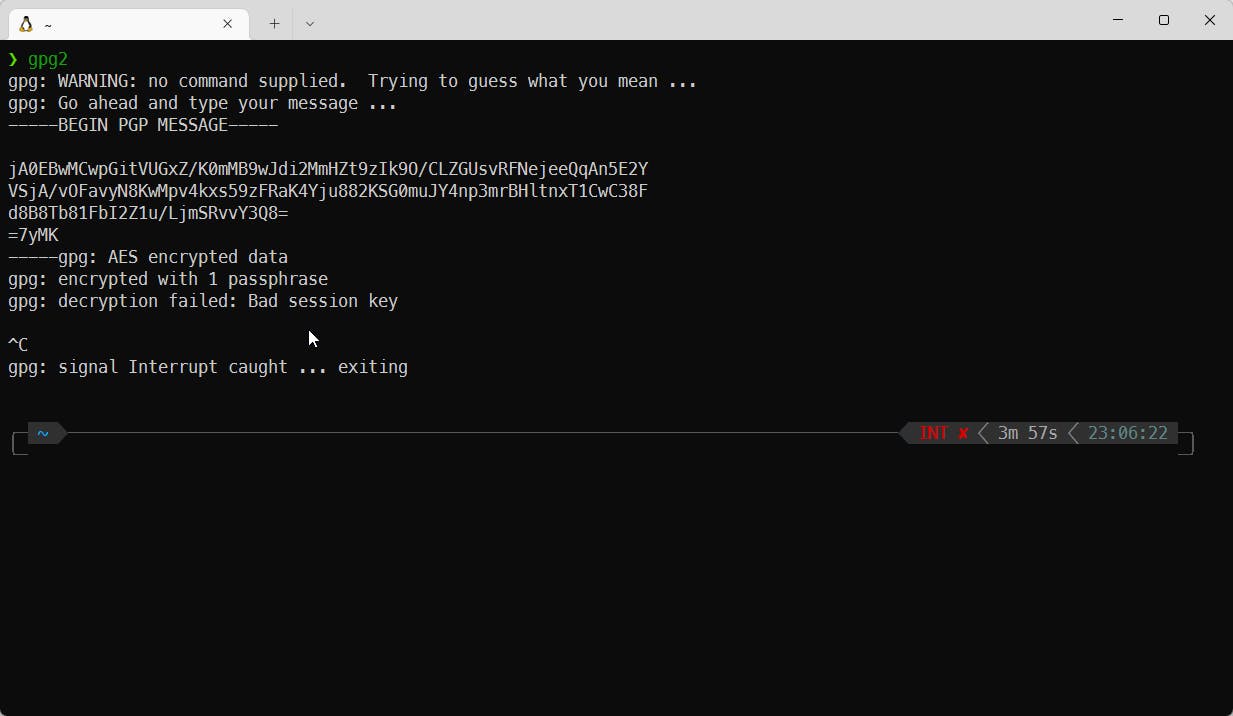
I tried to use multiple passwords, such as Silentless-X, Enigma-77, Silentless, Enigma, treasure, etc., but no luck there.
As I am (in fact) very-very-veeeeryyyy lazy, I decided to use other tactic. First attempt decrypting this message hints us, that it is am AES encrypted message. And you know what? It is an symmetric cipher and can bruteforced! All this because I am too lazy to guess the password
Bruteforcing with my friend John
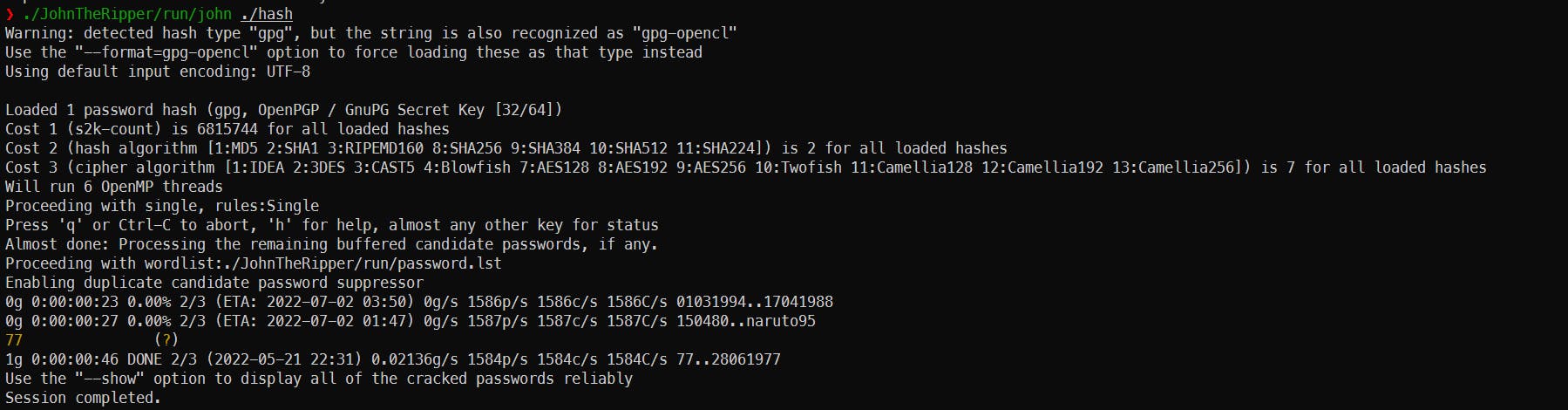
Such happened, that I know exact software to use in my case - John the Ripper. It is very capable software, commonly used to bruteforce different ciphers and hashes.
John the Ripper runs thousands of different passwords per second trying to guess the right password
Said, I am not an expert at using John, I asked Google for help. Quick googling for "john the ripper gpg aes" giving us the following article - openwall.com/lists/john-users/2015/11/17/1
So I did all the stuff, needed to run my bruteforcer, and here it is - password was 77 all that time, and I could've easily guessed it!
3. Caesar, but not a salad
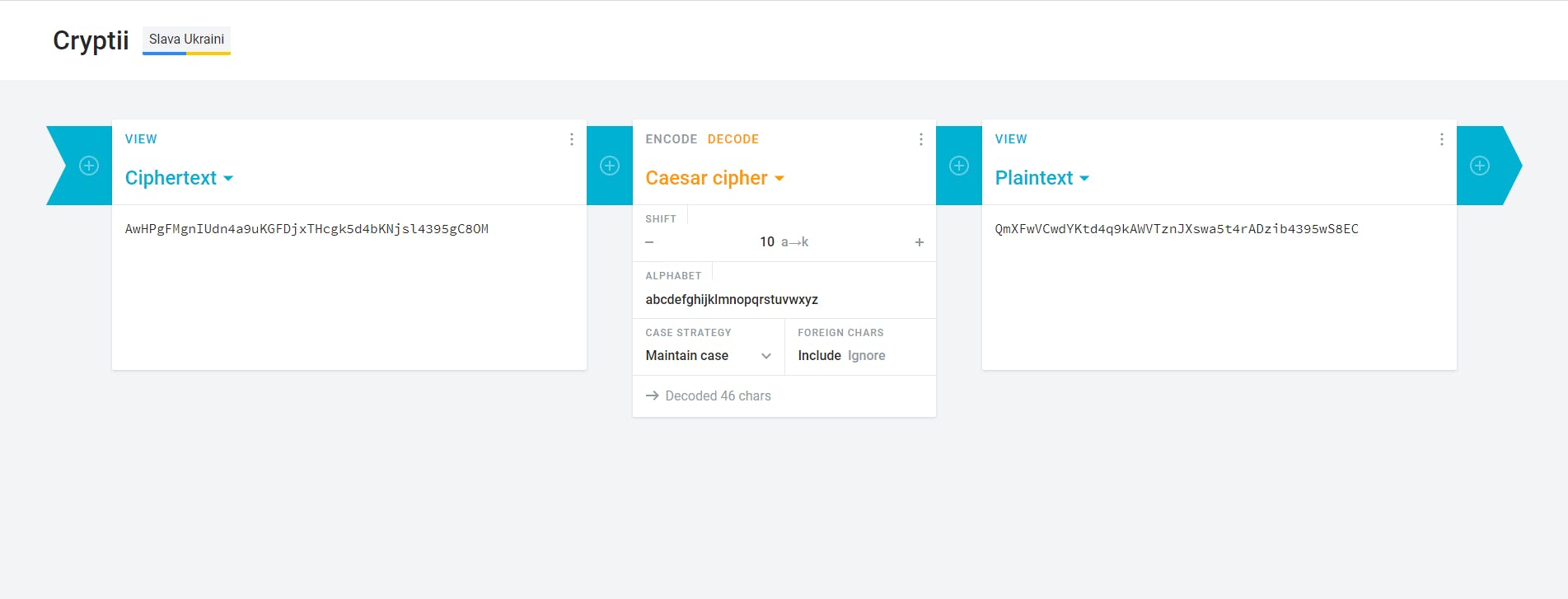
Finally decrypting PGP message with correct passwords giving us the weird combination of symbols: AwHPgFMgnIUdn4a9uKGFDjxTHcgk5d4bKNjsl4395gC8OM
Thanks, Hertz, for hints in his Discord announcement, I knew before even acquiring this gibberish, that the easiest of all ciphers will be used in this riddle - Caesar cipher.
Caesar shift, is one of the simplest and most widely known encryption techniques. It is a type of substitution cipher in which each letter in the plaintext is replaced by a letter some fixed number of positions down the alphabet. For example, with a left shift of 3, D would be replaced by A, E would become B, and so on.
Once again, I used first tool, that showed up in google for "caesar cipher online" and now we have... another gibberish: QmXFwVCwdYKtd4q9kAWVTznJXswa5t4rADzib4395wS8EC
4. IPFS and HTML
IPFS
Once again, thanks Hertz, I've seen this thing already, when X-Map was discovered, so I just typed into my Brave Browser ipfs://QmXFwVCwdYKtd4q9kAWVTznJXswa5t4rADzib4395wS8ECand was presented by link to GitHub repository
HTML
Opening GitHub repo resulted in HTML project, and I was asked to run it on my local server. But I am a developer, I can interprete HTML in head! And after a quick code read, I got asked to open a discord ticked and tell what I did there!
Reward
As a reward for solving this riddle, I got this awesome E-77 token and became first of 77 Enigmas!
What is Silentless-X and Enigma-77?
Silentless-X is a closed web3 community, focused on sharing knowledge with others. You can join Silentless-X community by acquiring X-Key from OpenSea:
Post Scriptum
Don't be afraid not knowing something, look at this as an opportunity to learn something new!

